CUI Overview and History Controlled unclassified information, or CUI, is sensitive information ... Read More

The steps to CMMC compliance form a huge undertaking. Gain valuable insight about CMMC requirements, getting an accurate assessment, remediating gaps in compliance, and passing your certification audit.
Navigate to a post category:
NIST SP 800-171 cybersecurity standards are well-known, widely accepted, and are integral in the foundation of the CMMC model.

CUI Overview and History Controlled unclassified information, or CUI, is sensitive information ... Read More

There are several different types of cybersecurity assessments. For CMMC, there are ... Read More

While the CMMC framework is managed directly by the DoD, the ecosystem ... Read More

In the past three years, the number of cyber incidents reported has ... Read More

What is DFARS? The Federal Acquisition Regulation (FAR) is the primary set ... Read More
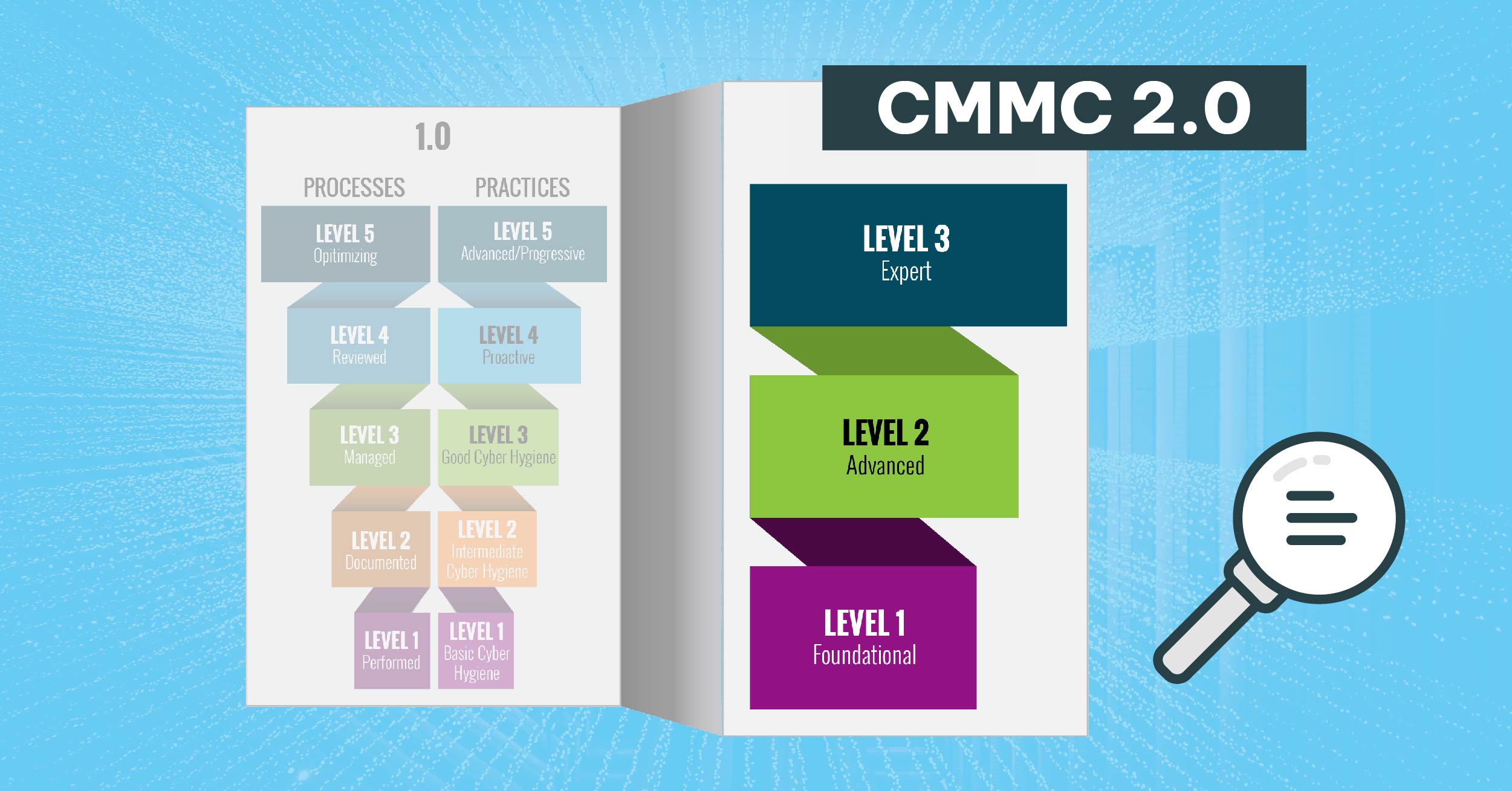
This post contains information regarding the CMMC 2.0 model.The DoD is in ... Read More

This post contains information regarding the CMMC 2.0 model.The DoD is in ... Read More

Wherever you can find information about CMMC, the term “NIST SP 800-171” ... Read More

Safeguarding the sensitive non-classified information that is shared with U.S. defense contractors ... Read More

Cybersecurity is the protection of computer systems, networks, and data from unauthorized ... Read More
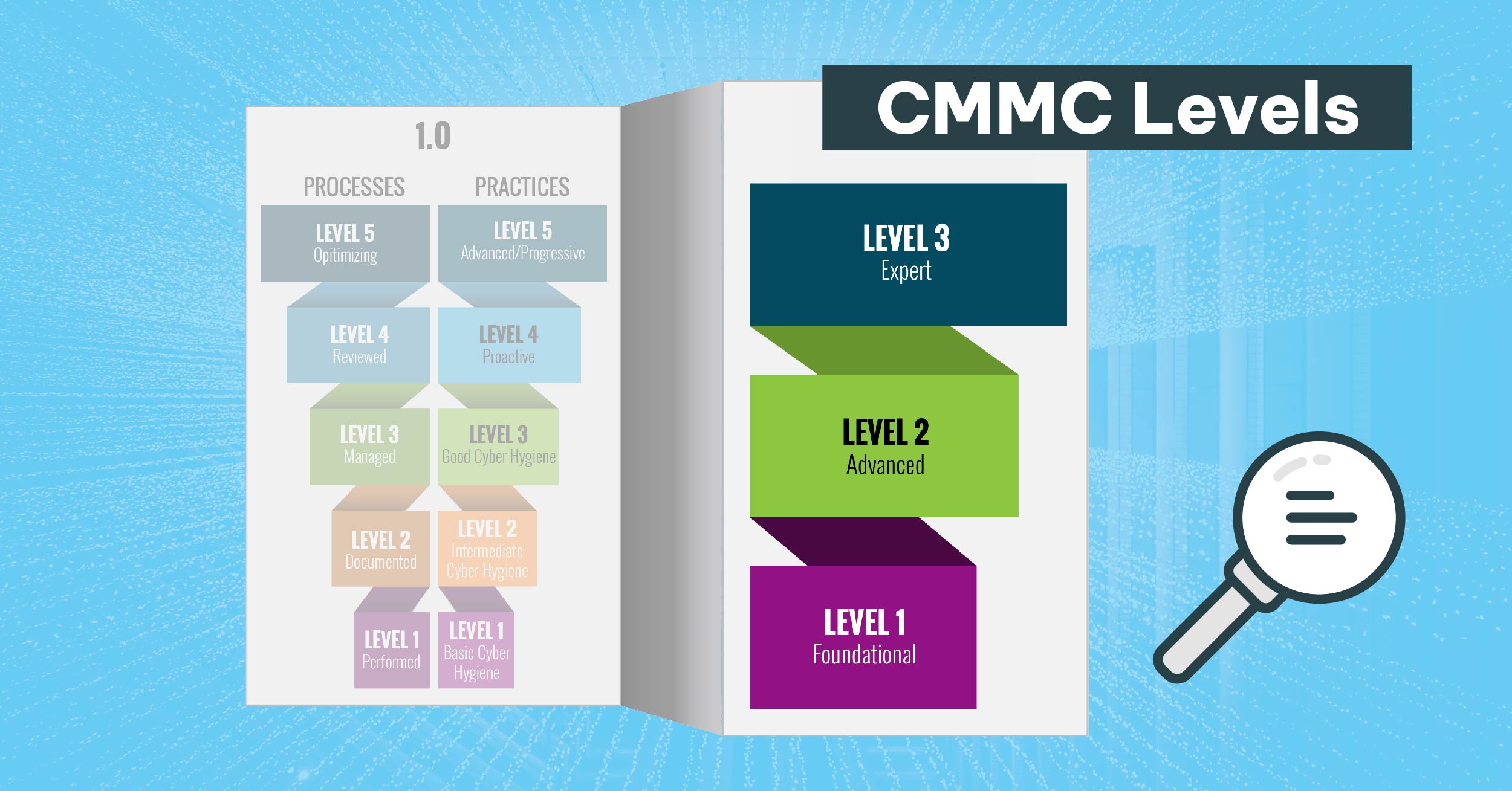
This post contains information regarding the CMMC 2.0 model.The DoD is in ... Read More